Phishing “Y Combinator” invites to drain crypto, the takedown of America’s largest SIM farm, and other cybersecurity news

The week’s key cybersecurity developments.
- Blockchain developers downloaded a crypto-stealer nearly 8,500 times.
- A crypto drainer was found in fake invitations to Y Combinator’s accelerator.
- A new macOS malware targets developers’ cryptocurrency.
- The US Secret Service dismantled the largest SIM farm near UN headquarters.
Blockchain developers downloaded a crypto-stealer almost 8,500 times
Two malicious packages in the official repository for the Rust programming language scanned developers’ devices to steal cryptocurrency and sensitive information. Since May 25, 2025, they had been downloaded 8,424 times. Socket security researchers reported this on September 24.
The malware, faster_log and async_println, spread via the Crates.io registry, the equivalent of npm for JavaScript. They impersonated the legitimate fast_log, copying its README and repository metadata. The impostor even preserved the logging function of the real project to reduce suspicion.
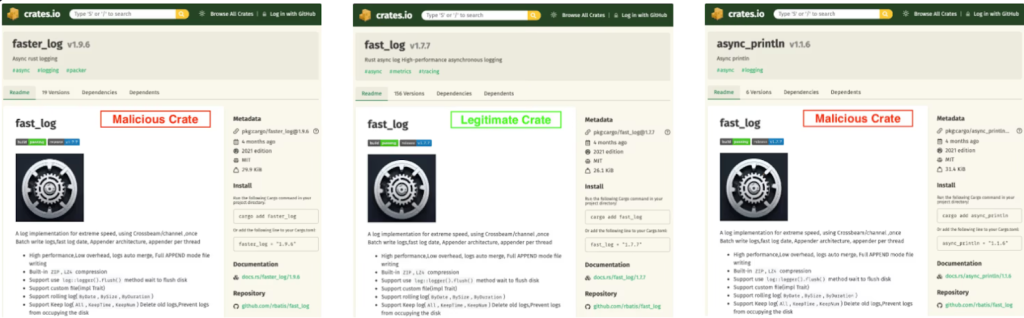

The malware scanned the victim’s environment and project source files for:
- hexadecimal strings resembling Ethereum private keys;
- Base58 strings suggestive of Solana keys and addresses;
- byte arrays in brackets that could conceal seed phrases.
When a match was found, the code exfiltrated the data to an encoded URL.
The platform removed the fake packages and blocked the perpetrators’ accounts the day it was notified.
A crypto drainer found in Y Combinator accelerator invites
A large phishing campaign targeted GitHub users via cryptocurrency drainers delivered through fake invitations to Y Combinator’s startup support programme.
On September 24, BleepingComputer reported that attackers abused shortcomings in the notification system to deliver fraudulent messages. They created issues across multiple repositories and mentioned targeted users.
When a username is mentioned in GitHub issues, the platform automatically sends a notification. Because the message comes from a legitimate source, it lands directly in the inbox.
The lure was an invitation to apply for an upcoming Y Combinator funding round with a $15 million fund. In some repositories, up to 500 issues were opened by a user who had registered only a week earlier.
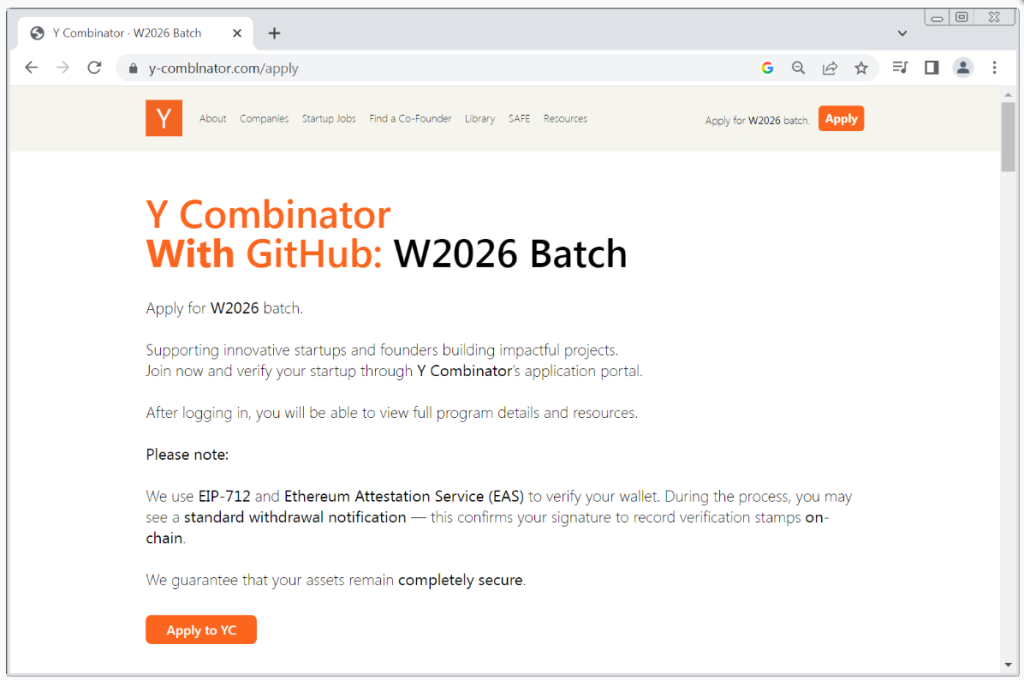

Recipients were prompted to follow a phishing link. The fake domain contained a barely noticeable typo (“l” instead of “i”). After clicking, JavaScript prompted a crypto-wallet verification; signing triggered malicious transactions that drained accounts.
Following complaints to GitHub, IC3 and Google Safe Browsing, the fraudulent repositories were removed.
A new macOS malware targets developers’ cryptocurrency
On September 25, Microsoft Threat Intelligence identified a new variant of the XCSSET malware for macOS, built to steal notes, cryptocurrency and browser data from infected devices. It spreads by finding and infecting other projects in the Xcode development environment, executing during the build process.
“We believe that this infection and propagation method is based on the sharing of project files among developers creating applications for Apple or macOS,” the experts’ report says.
Researchers noted several changes in the new stealer:
- a focus on Firefox browser data and the installation of a modified build of HackBrowserData, which decrypts and exports data from stores;
- an updated macOS clipboard hijacker that parses regular-expression patterns related to cryptocurrency addresses;
- when a crypto wallet is detected, it is swapped for a fraudulent one.
The US Secret Service dismantled the largest SIM farm near UN headquarters
On September 23, the US Secret Service announced an operation in which the largest SIM farm in the country’s history was found and neutralised.
According to The New York Times, the investigation began after senior officials started receiving anonymous threatening calls earlier this year. The victims included two White House staffers and one Secret Service employee.
More than 300 combined SIM servers and 100,000 SIM cards were seized. The farm operated 56 km from UN headquarters, where the General Assembly was meeting with world leaders. Agents neutralised the farm a few hours before the session.


The farm’s capacity allowed spam to be sent to virtually all US phone numbers within minutes, as well as to take down the entire national telecommunications network.
Investigators found empty safe houses rented in Armonk (New York), Greenwich (Connecticut), Queens (New York) and New Jersey. Agents also seized firearms, computers, mobile phones and 80 grams of cocaine.
First leads emerge in the attack on European airports
On September 24, a suspect in distributing ransomware that caused major disruptions at European airports was arrested.
A man has been arrested in the UK by the NCA as part of an investigation into a cyber incident impacting Collins Aerospace.
Read the full story ➡️ https://t.co/v70Ullml4v@SouthEastROCU pic.twitter.com/v2DL1st9SC
— National Crime Agency (NCA) (@NCA_UK) September 24, 2025
Law enforcement said the arrest followed an investigation into a cyberattack that affected the Multi-User System Environment (MUSE) software from Collins Aerospace. The suspect was released on bail pending the investigation.
The attack was detected on Friday, September 19, when the first reports of flight delays appeared. Affected hubs included London Heathrow, Brussels Airport, Dublin Airport, Berlin Brandenburg Airport and others.
Interpol seizes $439 million in cryptocurrency and cash
In an international operation led by Interpol, law enforcement seized more than $439 million in cash and cryptocurrency. Authorities believe the confiscated funds are linked to cybercrimes that harmed thousands of victims worldwide.
The operation, codenamed HAECHI VI, ran from April to August with authorities from 40 countries. Investigators seized 400 crypto wallets and blocked more than 68,000 associated bank accounts. Around $16 million was confiscated in cryptocurrencies.
As part of the operation, Portuguese authorities arrested 45 suspects for illegal access to social-security accounts. In addition, Thailand’s Royal Police seized $6.6 million that an unnamed Japanese corporation had transferred to accounts controlled by a transnational criminal group of Thai and West African nationals.
Also on ForkLog:
- DeFi protocol Hypervault “vanished” with $3.6 million in cryptoassets.
- Media: the SEC and FINRA launched an investigation into DAT companies.
- Ethereum co-founder urged replacing closed systems in healthcare and finance with open solutions.
- The hacker who breached UXLINK became a victim of an attack.
- Bloomberg reported a previously undisclosed Crypto.com breach.
- Solana’s founder warned that the quantum threat to bitcoin is real.
Нашли ошибку в тексте? Выделите ее и нажмите CTRL+ENTER
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!
Credit: Source link






